Fixing the Zoom ‘Vanity Clause’ – Check Point and Zoom collaborate to fix Vanity URL issue

Research by: Adi Ikan, Liri Porat and Ori Hamama
Introduction
As the world starts to emerge from Coronavirus-related lockdowns, and organizations continue to support remote working for their employees, ’Zooming’ has become part of our everyday language. The video conferencing service was already popular before the pandemic, but in the ‘new normal’ of social distancing it has become the go-to platform globally for everything from high-level government and business meetings, to university and school classes, to family gatherings – meaning that Zoom usage has soared from 10 million daily meeting participants back in December 2019 to over 300 million in April 2020.
Of course, where people go, criminals will follow. So it’s no surprise that the explosive growth in Zoom usage has been matched by an increase in new domain registrations with names including the word ’Zoom’, indicating that cyber-criminals are targeting Zoom domains as phishing bait to lure victims.We have also detected malicious files impersonating Zoom’s installation program.
In our ongoing efforts to respond to the latest developments in the threat landscape and contribute to the global cyber security community, we have collaborated with Zoom Video Communications to find ways to ensure that its users can enjoy all of its benefits safely and securely. Back In January 2020 we reported a technique which would have allowed a threat actor to potentially identify and join active meetings to which they weren’t invited. As part of our cooperation, Zoom quickly introduced a number of mitigations which ensured that such attacks are no longer possible.
And recently we found another potential security issue, as described below, which could have led to successful phishing attempts. As a result of our continued collaboration and Check Point’s reporting of this issue,Zoom has resolved the issue with a fix.
The cost of vanity
One of the features of Zoom is the ability to create a ‘Vanity URL,’ which is described on the Zoom website as: A Vanity URL is a custom URL for your company, such as yourcompany.zoom.us. In addition, the organization can add a dedicated and customized website for this service.
The Vanity URL mechanism allows organizations to create a customized version of Zoom’s invitations links. Prior to Zoom’s fix, an attacker could have attempted to impersonate an organization’s Vanity URL link and send invitations which appeared to be legitimate to trick a victim. In addition, the attacker could have directed the victim to a sub-domain dedicated website, where the victim entered the relevant meeting ID and would not be made aware that the invitation did not come from the legitimate organization.
The security issue with the vanity URL mechanism
The security issue is focused on the sub-domain functionalities described above. There are several ways to enter a meeting containing a sub-domain, including using a direct sub-domain link containing the meeting ID, or using the organization’s customized sub-domain web UI. Let’s look at each option in turn.
Direct link capability
This scenario targeted the Vanity URL capability. Upon setting up a meeting, an attacker could change the invitation link URL to include any registered sub-domain. For instance, if the original invitation link washttps://zoom[.]us/j/7470812100, the attacker could change it tohttps://[.]zoom[.]us/j/7470812100. A victim receiving such an invitation would have had no way of knowing the invitation did not actually come from the actual organization.
In addition, the attacker could also change the link from /j/ to /s/:https://[.]zoom[.]us/s/7470812100. Given there are cases of organization’s logos appearing when entering such a URL, this could have added an additional layer of deception. Also, clicking on the “Sign in to Start” button, would often lead the victim to the organization’s legitimate portal. This issue impersonated relevant organizations using the Vanity URL capability.
Organizations’ dedicated web UI
Another way of entering a meeting is with the organization’s dedicated sub-domain web UI, as seen in the example below:
Figure 1 – An organization’s Zoom Web UI


When the user enters the website and clicks the Join button, the following screen appears:
Figure 2 – Zoom’s ‘Join a Meeting Screen’
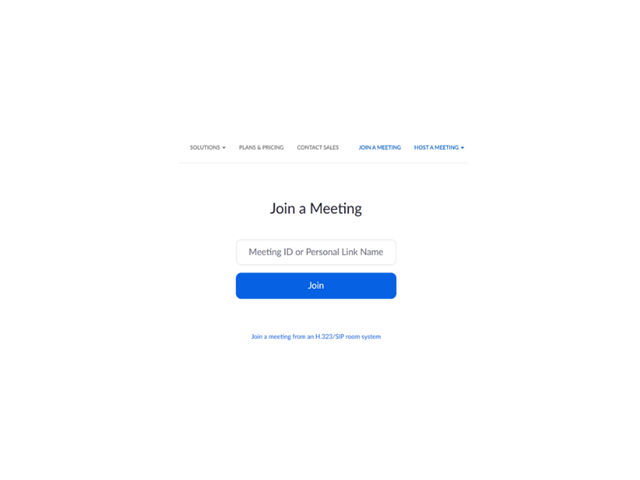

A user can enter any meeting ID in this screen, whether it was originally scheduled by the organization’s employee or not, and join the relevant Zoom session. An attacker could have invited the victim to join the session through the dedicated website, and the victim would have had no way of knowing the invitation did not actually come from the legitimate organization.
Impact
There are many relevant day-to-day scenarios that could potentially have been leveraged using this impersonation method, which could have resulted in a successful phishing attempt – Especially if used to impersonate an enterprise’s Zoom Vanity URL.
For example, an attacker could have introduced themselves as legitimate employees in the company, sending an invitation from an organization’s Vanity URL to relevant customers in order to gain credibility. This activity could have then been leveraged to stealing credentials and sensitive information, as well as other fraud actions.
Mitigation & Summary
All the details of how an attacker could impersonate an organization’s Zoom subdomain links or actual sub-domain website discussed here were responsibly disclosed to Zoom Video Communications, Inc. as part of our ongoing partnership and cooperation. This security issue has been fixed by Zoom, so the exploits described are no longer possible.
Adi Ikan, Network Research & Protection Group Manager in Check Point: “Our partnership with Zoom has provided Zoom users globally with a safer, simpler and seamless communication experience. cp<r> is dedicated to improve and thrive towards safer technologies, better secured infrastructures, and generally to enrich the greater intelligence community, and will continue such efforts by liaising with product leaders such as Zoom”
It’s worth noting that 90% of cyber-attacks start with a phishing email. To make sure you’re doing enough to protect your organization’s attack vectors, we suggest that you read the whitepaper Humans are Your Weakest Link to discover the daily risk posed by phishing emails.
Also, to enjoy the various benefits of daily usage of Zoom, here are some guidelines to consider. Happy Zooming!





