The complete guide to email security
By ANDRA ZAHARIA SECURITY EVANGELIST
From Heimdal Security
When your alarm goes off in the morning, what’s the first thing you check?
Most people will tap on one of two apps: their email app or their go-to social media account. You probably can’t even remember what your morning routine looked like before this. I know I can’t.
For most of us (myself included), email is our digital home. That’s where we keep our contacts for the people we love and for the people we work with. It’s where we hoard newsletters subscriptions and wishlists, pictures and documents, love and hate digital letters and SO much more.
So no matter what click-bait titles tell you, email is not dead. Not at all!
In fact, people all over the world rely on email for a big chunk of their communication. In 2015, 205 billion emails travelled from outbox to inbox every single day (Radicati Group research).
This is how many email accounts existed in 2015 and predictions show that the number is set to increase by almost 30% until 2019.
Not only is email alive and thriving, but we’ve actually started using it more intensely since we started having smartphones for hands.
Email is deeply tied to our online identities. We use it to set up accounts, to verify logins, to keep track of deliveries, to get alerts from services, to complain about things and to share info. So it shouldn’t come as a surprise that cyber criminals want to get in your inbox. Here is a handy timeline of the worst cases of email security breaches, one that shows just how pervasive this issue is.
The problem with email security comes from two sources: users who don’t pay enough attention to password safety (poor passwords, reused) and companies which are careless with their users’ confidential data (storing passwords in plain text, etc.). When these issues overlap, everyone gets hurt.
In the past years, cyber criminals have hacked companies from all over the world, exposing millions of email accounts and their passwords.
2015 – 000webhost suffers a massive data breach and 13 million customers have their personal information stolen, including emails, usernames and passwords stored in plain text
2014 – Yahoo gets hacked and at least 500 million account and their associated data (usernames, passwords, security questions, telephone numbers, etc.) are stolen
2008 – 360 million accounts exposed, including emails, usernames and key details about passwords
I could go on, but I’m sure you get the picture.
The point I’m trying to make is that email security is paramount for your digital safety. It’s actually more important than most of your online accounts, except your Internet banking account and a few others (websites you may have, work stuff, etc.).
Securing your email addresses is not that complicated. To prove this, we put together the guide below, to highlight key security settings you can make right now. Yahoo,Gmail, Aol and Outlook are the most popular free email solutions that people use all over the world, so we dedicated a step-by-step section to each one.
At the end of the article, you’ll find a dozen general guidelines to follow if you’re serious about keeping your email accounts safe.
If you want to quickly navigate between the sections, use the links below:
- Protect your Yahoo mail account
- Secure your Gmail account
- Shield your Outlook account
- Safeguard your AOL mail
- 12 general rules for better email security
Protect Your Yahoo! Mail Account
Yahoo’s email service is probably the most popular in the world, but they may lost this privileged position soon.
In late 2014, hackers stole information associated with at least 500 million Yahoo! user accounts. This breach was publicly disclosed by Yahoo two years later on September 22, 2016. The data breach is the largest discovered in the history of the Internet. Specific details of material taken include names, email addresses, telephone numbers, encrypted or unencrypted security questions and answers, dates of birth, and encrypted passwords.
Source: Wikipedia
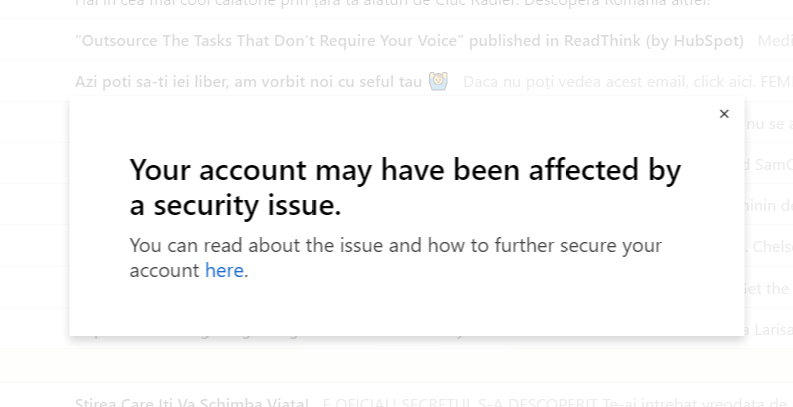
As a Yahoo email user myself, I definitely didn’t like seeing this warning in my inbox one fair morning.
Sadly, the issue actually runs deeper: in October 2016, Reuters revealed that Yahoo had granted access to the contents of users’ emails to US intelligence agencies, so they could scan for specific information.
To make a bad thing worse, Yahoo also disabled email forwarding, preventing users from moving their stuff to another provider.
Given these revelations, you may want to consider closing your Yahoo account, as the company doesn’t seem to be able to guarantee its users’ right to privacy and security. They could fix this in the future, but they failed to disclose a huge breach
However, you probably have tens or hundreds of accounts created with your Yahoo email address, so it’ll take a while before you can change that. You may even decide to stick to Yahoo, but please decide on it after you’ve read the articles I just linked to. Such a blatant disregard for users’ safety and privacy shouldn’t be taken lightly.
Here’s what you can do to protect your Yahoo email account, even if the company itself doesn’t seem able to hold its end of the deal.
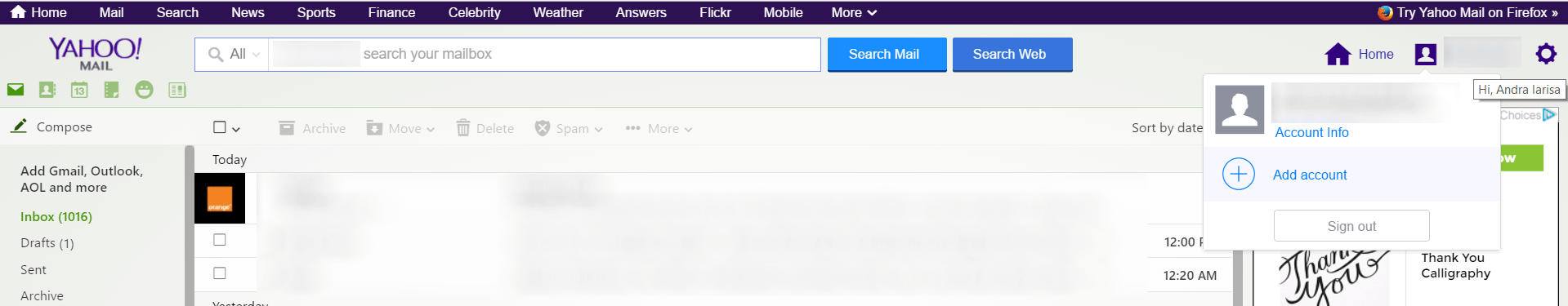
Log into your email account and go to Account Info:
It is important to add an alternative email address and a phone number so that you can be contacted in case of trouble.
Should you get locked out of your email account, you can have a recovery link sent to your alternate email address or get an SMS.
Go to Account security to add these details.
Oh, and since you’re here, you may want to change your password and make it a strong one.
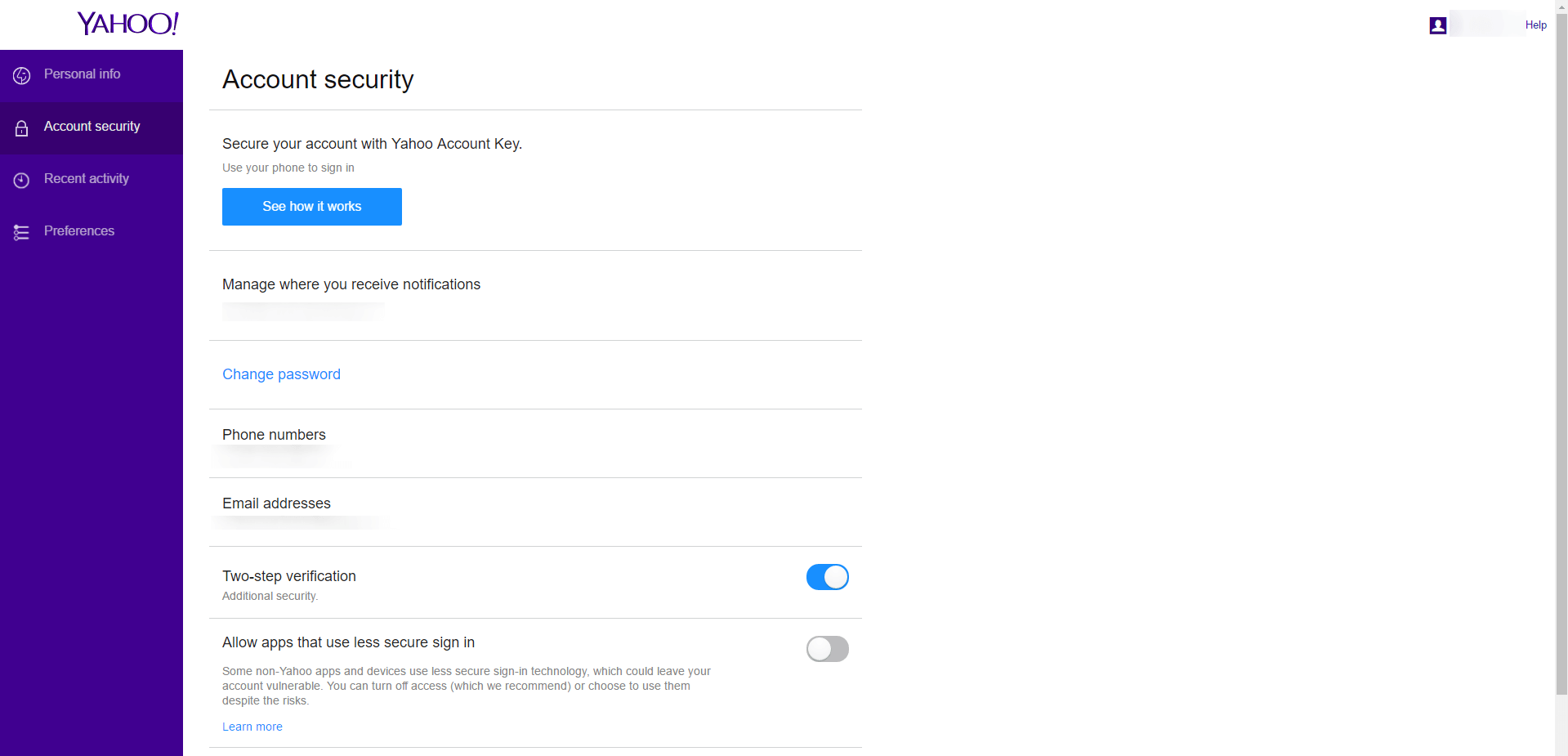
2. Set up two-step verification
This is probably the most important security setting you can set in your Yahoo account.
Two-step verification adds an extra level of protection for your email address. To activate this security step, you need to add your phone number to the Yahoo account.
Each time you log into your account from a new device, you’ll receive a code by SMS which provides additional verification to ensure that no one else can breach your account.
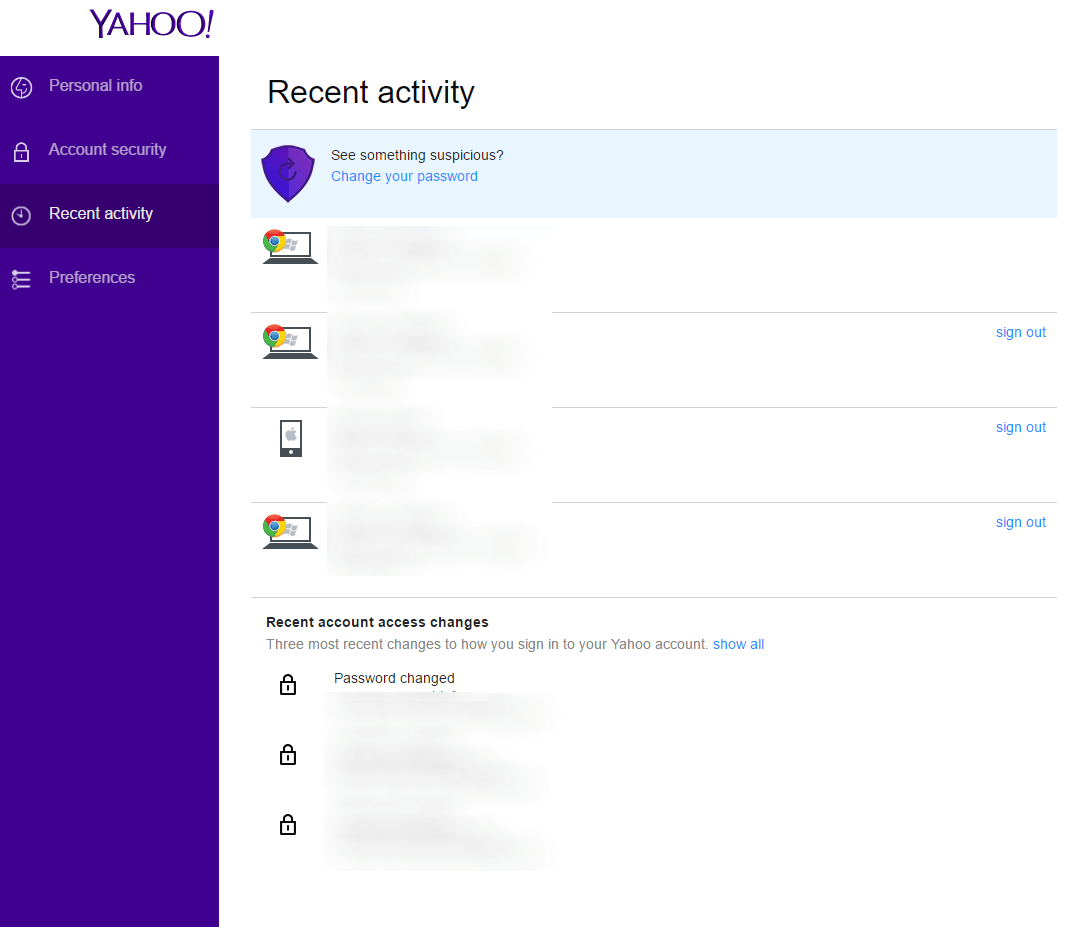
3. Verify your recent activity
Don’t forget to verify your account login history and make sure only you are connected to your email account.
You can also verify password changes here and sign out of devices you no longer use.
4. Deny apps that use less secure sign in
This is the place where you can also revoke access to apps that you connected to your Yahoo email account. These can be apps that make using Yahoo email easier or more organized.
We highly recommend you try not to grant access to any such apps and turn off “Allow apps that use less secure sign in”.
5. Secure your account with Yahoo Account Key
Another security feature you can enable is setting up your Yahoo Account Key. This key can replace your password.
You’ll no longer need to remember complicated passwords when you use Yahoo Account Key to access your account. To sign in, tap “Yes” on the notification we send to your mobile phone. With Account Key enabled, there’s no password on your account, so no one other than you can sign in.
You can read all about it on Yahoo help and test it yourself. However, if you lose your phone and it’s not password protected, anyone will be able to get in your inbox right away.
Secure Your Gmail Account
Gmail is one of the most trusted free email services on the Internet and it’s never been breached. Google has always spearheaded the way in security for its products and services, so they do take this aspect seriously.
So if you’re looking to enhance your Gmail account’s safety, here’s what you should do.
Reminder: when you set up a Gmail account, you automatically get a Google account, which is used for all Google products and services. This is your integrated identity and the security measures you apply for it are enforced for all the Google products and services you’ll use.
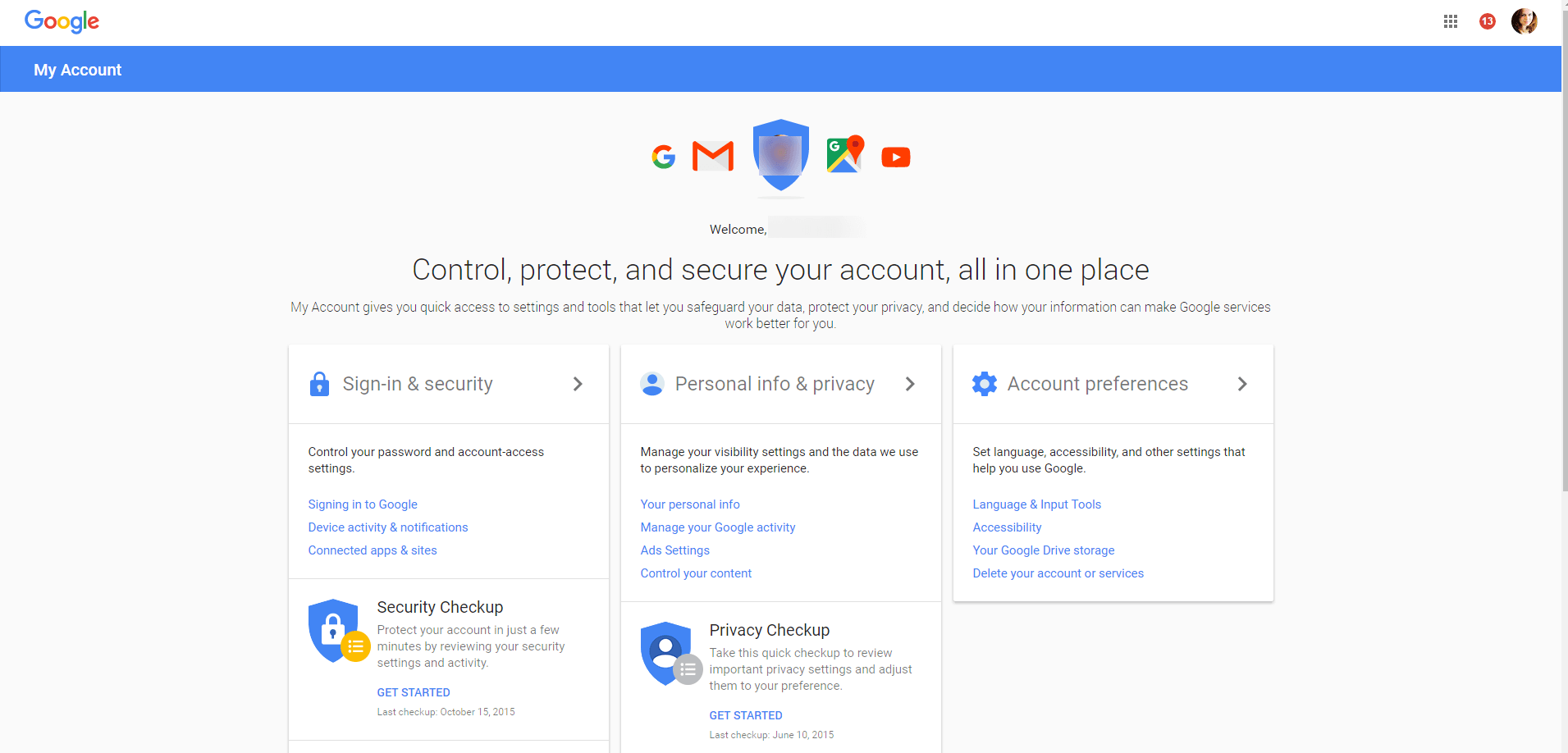
Google also makes it simple to secure your account. All you have to do is log into Gmail and go to My account.
Here, you’ll be able to easily do any of the following:
- Review sign-in and security
- See your personal info and privacy settings
- Set your account preferences
- Do a thorough Security checkup of your account
- Do a detailed Privacy Checkup
- Find your phone (if you have an Android device, of course)
- And review your activity.
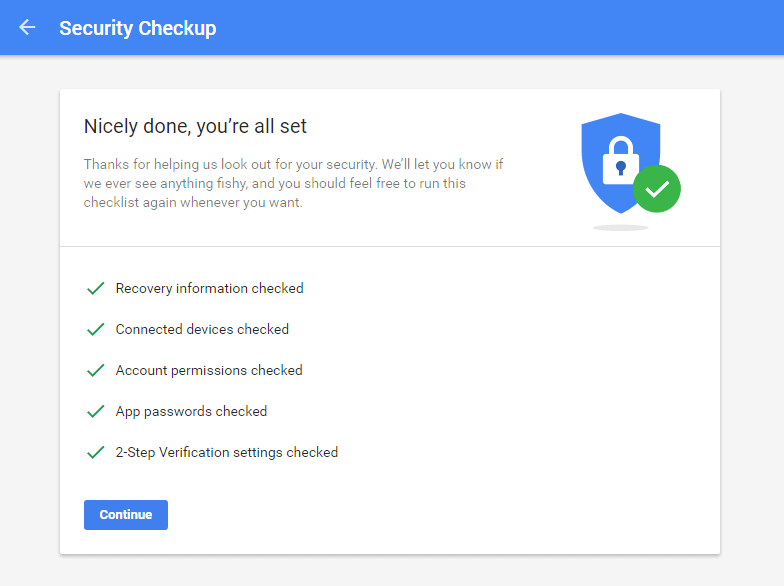
1. Do the Security checkup
This is the best way to get started. Here you can:
- Check your recovery information: alternate email address and phone, so Google can contact you in case of suspicious activity in your account or if you accidentally get locked out.
- Check your connected devices: see if you’re logged into devices you don’t recognize and immediately sign out of those devices.
- Check your account permissions: “review the apps, websites, and devices connected to your Google Account”. See which app has access to what and remove certain apps, websites and devices if you no longer use them.
- Check your app passwords: here you can “generate passwords for apps that don’t use 2-Step Verification”. You should only use this feature for apps you really, deeply trust. (If you’re security savvy, you’ll know not to trust any apps.)
- Check your 2-step verification settings: see if your backup phone is correct and how many backups codes you have left. Should you want to change your 2-step verification settings, go to this page.
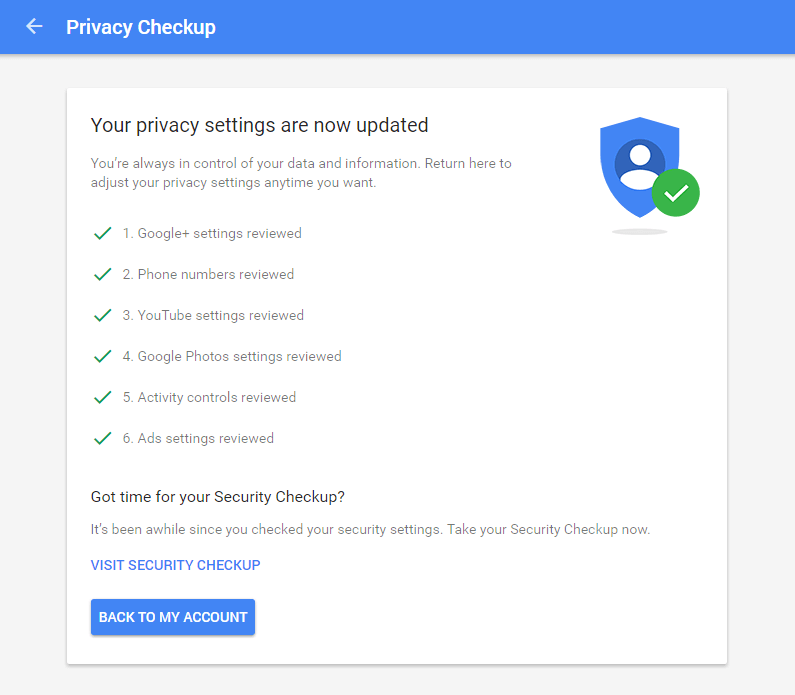
2. Do the Privacy Checkup
Privacy and security go hand in hand, so I recommend you check your privacy settings as well.
During this checkup, Google provides you with the opportunity to:
Choose what Google+ profile information you share with others: decide if you want others to see your photos, Youtube videos, +1s (if you still use Google+, of course) and reviews.
Help people connect with you: do you want people who have your phone number to find you and connect with you on Google services? If not, just uncheck the box. (We recommend you keep this feature turned off.)
Manage what you share on YouTube: this is where you can “choose who can see your YouTube videos, likes, and subscriptions, and decide where you share them.”
Manage your Google Photos settings: this is an important one, especially if you use Google photos to back up your pictures. I recommend you turn on this setting: “Remove geo location in items shared by link.”
Personalize your Google experience: tell Google if you want it to save information such as web & app activity, location history, device information, Youtube search history, voice & audio activity.
Make ads more relevant to you: here you get to tell Google which topics interest you and if you want to share your profile (gender and age segment), so you can get better recommendations.
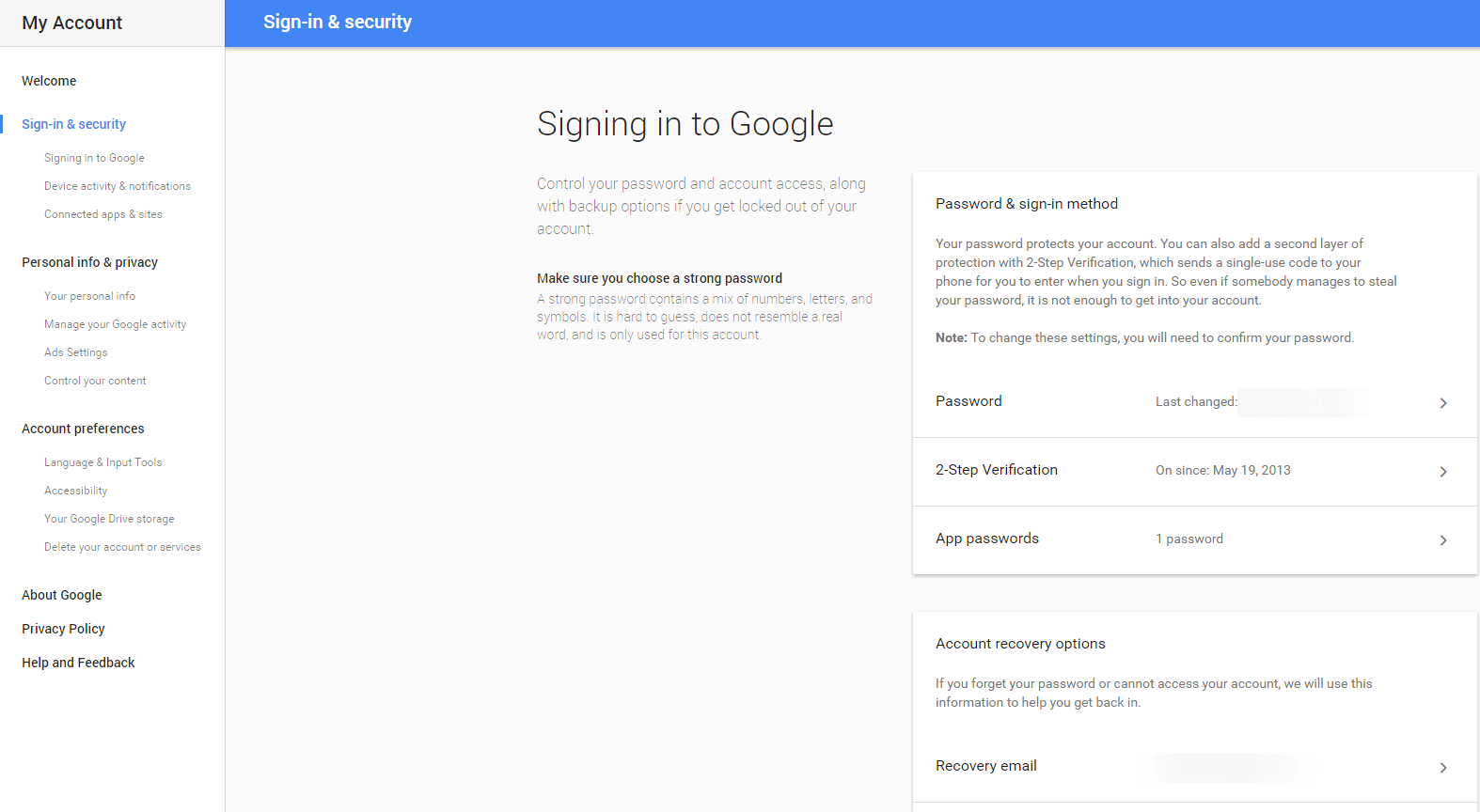
3. Review your sign-in & security settings
SIGNING IN TO GOOGLE
This is the most important section for your Gmail account’s safety. You can set up or change your password (and see when it was last changed), you can enable 2-step verification, you can define app passwords and set up account recovery options (alternate email and recovery phone).
Go over these details carefully and keep them up to date.
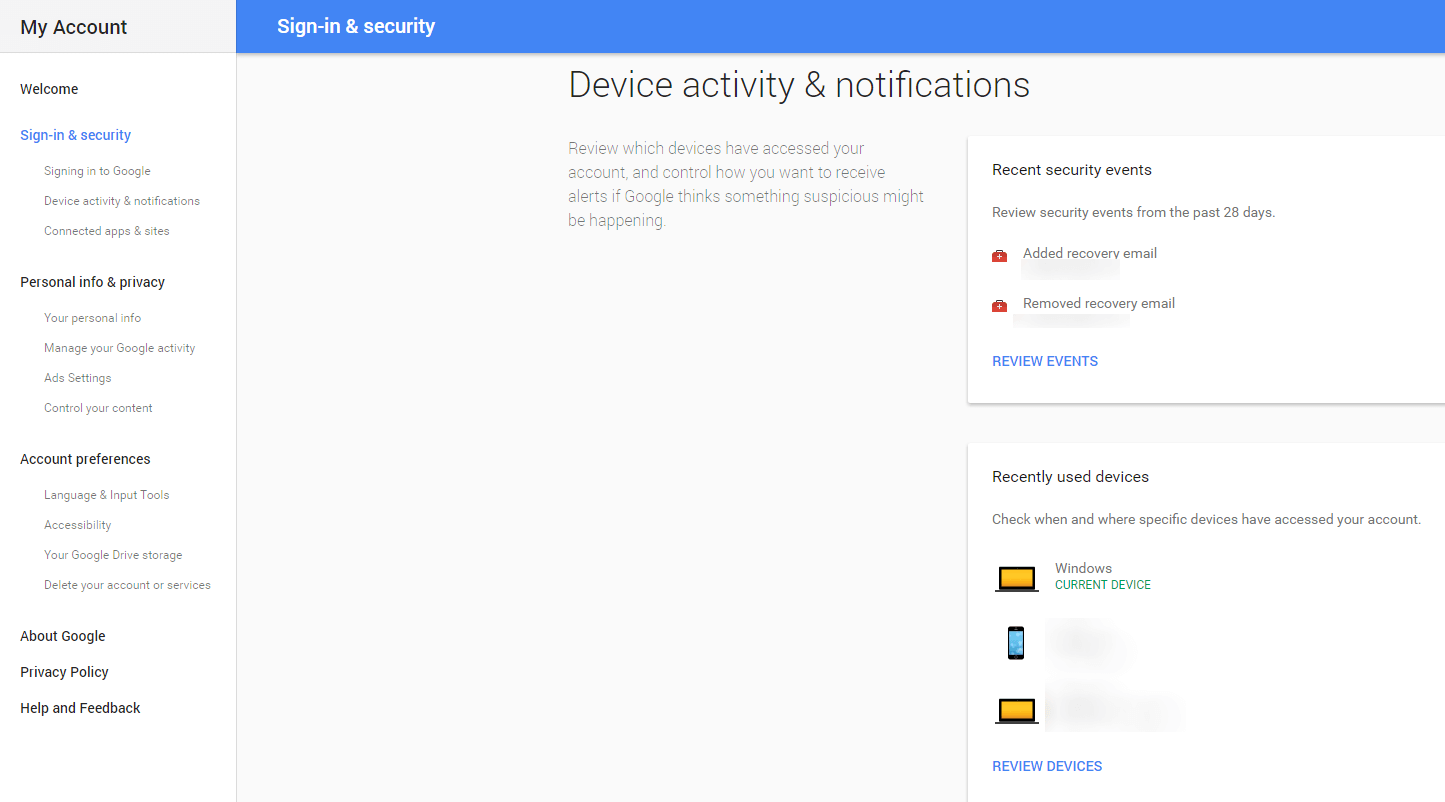
DEVICE ACTIVITY & NOTIFICATIONS
Take your time to review the recent security events associated with your account (any changes in password, recovery options, etc.). Also, see your recently used devicesand check for suspicious activity.
Here you can also modify your security alerts settings to tell Google it should email you or send you an SMS in case of critical security risks and other account activity issues.
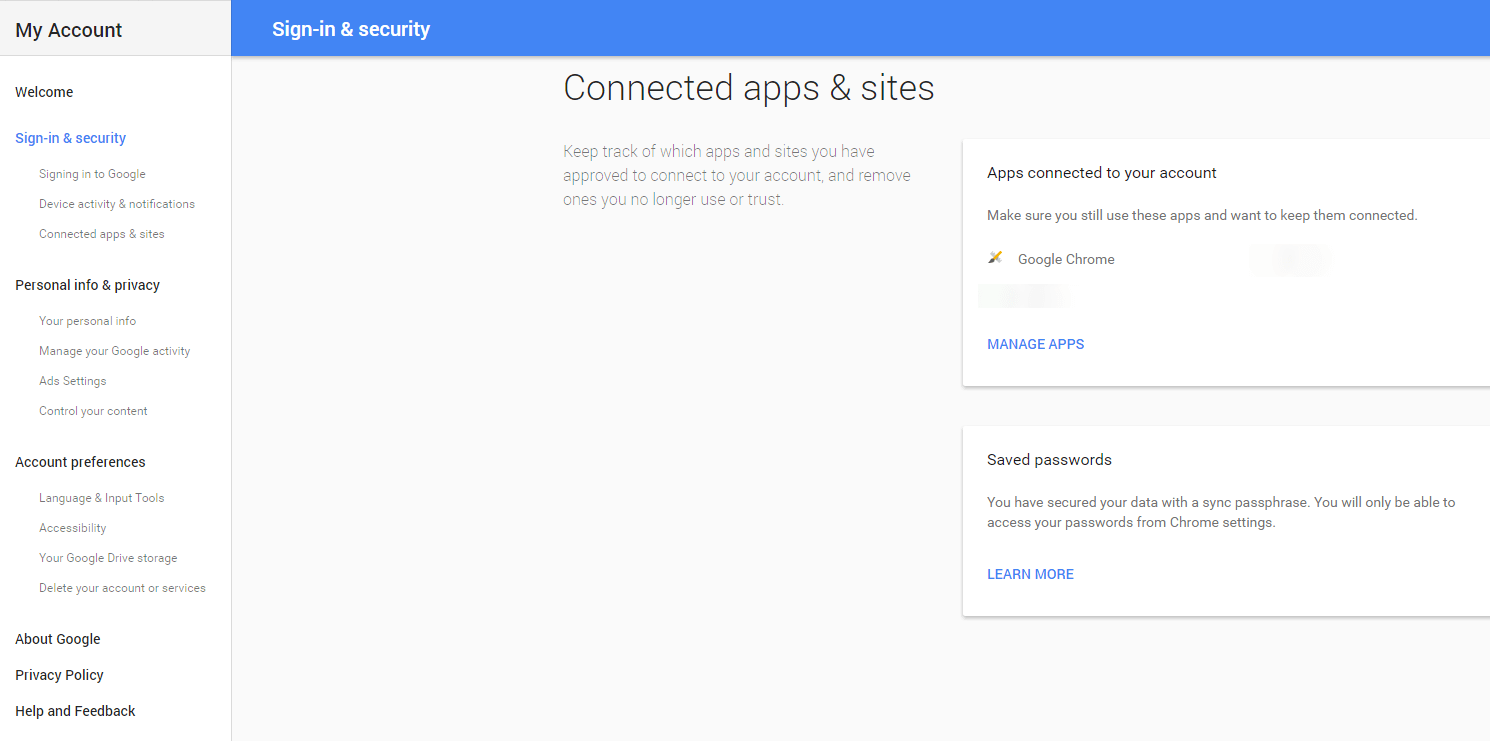
CONNECTED APPS & SITES
Check which apps are connected to your account and manage your saved passwords in Google Chrome. I highly recommend you never, ever save passwords in Chrome. It’s unsafe and you should use a password manager instead.
If you want to read more about how Google handles your data’s security, this is a useful resource.
Shield your Outlook web account
Outlook web is a strong option for those seeking to use a simple to use and reliable email platform for free. I’ve moved to Outlook after leaving Yahoo for things like newsletter subscriptions, setting up accounts, etc. (but not my main things, like online banking – that’s what Gmail is for).
Microsoft is also quite keen on security, so you’ll find there are plenty of options you can see to keep your inbox safe from cyber threats.
Outlook has the same approach as Gmail – your Outlook account is also your identity for all Microsoft services and products. The same way as mentioned before, all the security settings you apply for your profile will have an effect on your profile across all Microsoft platforms.
1. Access your profile settings
First, you have to log into Outlook web and click on your profile picture and go to View Account.
Here, you’ll get a bird’s eye view of your key settings:
- You can change your password
- See which devices you’re connected on and where they’re located
- And get help with your Microsoft account.
Next, go to Your info and Manage how you sign in to Microsoft. Clicking on this will lead you to a separate page, where you can set up/change your primary account aliasand change your sign-in preferences.
An account alias is an email address or phone number that you use to sign in to your Microsoft account. You can have multiple aliases, and use any of them with Microsoft services such as Outlook.com, Skype, OneDrive, Office, Xbox, Windows and more.
Your account’s primary alias is displayed on your Microsoft devices (such as a Windows PC, Xbox or Windows Phone), and you can choose a different alias to be the primary one at any time. Learn more about account aliases.
2. Tighten your security and privacy settings
The most important section for your Outlook account’s safety is Security & Privacy. This is where you can:
- Change your password
- See your recent activity
- Explore more security settings
- Manage permissions for other apps connected to your account
- And find out how Microsoft uses your data.
When you go to More security settings, you’ll find the following options:
- Change your password
- Set up alternate email addresses and phone numbers
- Modify your security alert options
- Change sign-in preferences
- Set up two-step verification
- Set up the Microsoft identity verification apps (learn more about identity verification apps)
- Create app passwords
- Replace your account recovery code
- Review your trusted devices
- And close your account (if you want to).
It’s all rather simple, so I’m sure you’ll have no challenge in building up your account’s security.
Safeguard your AOL mail
The AOL mail service is still quite popular among Internet users, especially in the United States.
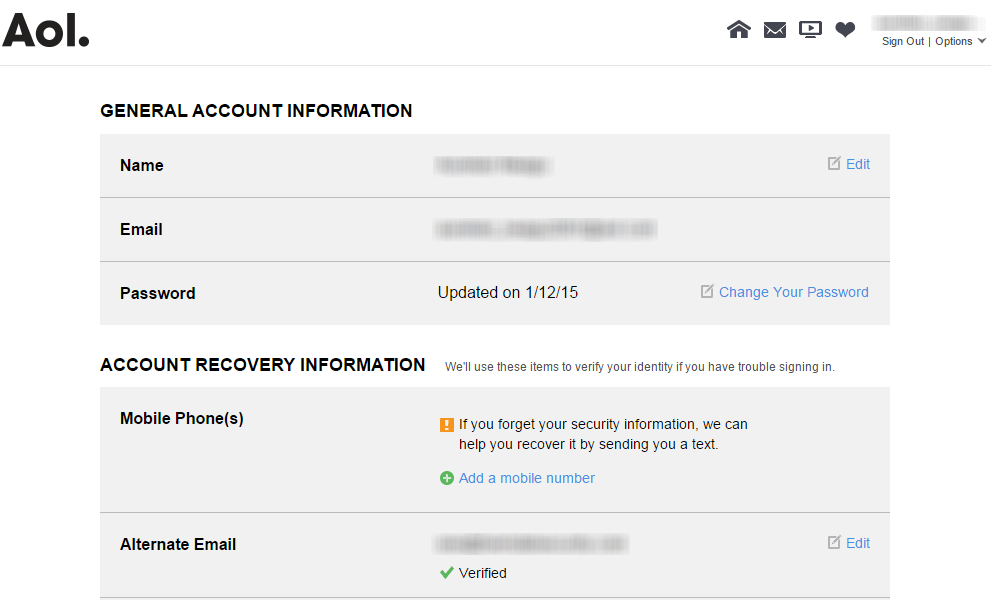
If you want your AOL account to be safer, you’ll need to access your general account information.
Follow these steps:
1. Access your Account Info from the top right corner.
2. You may need to put in the answer for your secret question before getting access to the General account information.
In this section, under Account Recovery Information, you’ll find the option to add an alternative email address and a phone number. These will be used to contact you in case a security issue comes up.
Aol also has a page dedicated to helping you make the right decision if your account has been hacked or if you’ve noticed any suspicious activity in your inbox.
12 general rules for better email security
Adjusting your security settings for each of your email accounts is a must, but don’t stop there if you’re serious about your inboxes’ safety.
Being keen on your online safety means developing a proactive and cautious mindset. Here are a dozen more things you can do to keep your inbox safe and sound:
1. Separate your email addresses.
To limit the impact that a cyber threat can have on your inbox, I recommend you set up at least 2 email addresses. You can either separate them according to professional and personal use or keep one for sensitive accounts and use the other for things like newsletter subscriptions and other trivial matters.
At the same time, you’ll need at least 2 email addresses, so you can use one as an alternate.
Key advice: never, ever reuse passwords and never, ever, ever set the same password for your email addresses.
2. Put a bit of effort into your password hygiene
A good password is long and complicated. It’s also difficult to remember. But password management doesn’t have to be complicated, if you know how to handle it.
Use a password manager and forget about your worries.
Also, make sure you enable two-factor authentication whenever it’s available. If it’s not, maybe you should reconsider your choice of email provider.
3. Protect your smartphone
Because I mentioned two-factor authentication, I have to remind you that this security layer depends on how well you secure your smartphone.
If you don’t use a password to protect your phone (or a fingerprint password), anyone will be able to read your SMS codes for two-factor authentication. Weak passwords that are easy to break combined with this type of mishap can turn into a nightmare.
Security depends on multiple elements working together. Like the pieces of a puzzle, you can’t have one without the other.
4. Log into your email accounts from a secure browser
Securing your inbox also depends on how you access it. Make sure the browser you use is up to date and safe.
Outdated browsers are cyber criminals’ favorite target. One vulnerability could allow them to launch Man-in-the-Middle attacks and steal your email username and password, for example.
Adjusting your browser’s privacy and security settings is also a good idea and we have just the guide for that!
I don’t recommend logging into your email account from public PCs or computers and devices which you don’t personally own. This could pose a huge security risk which is just not worth taking.
5. Don’t connect apps to your email account
Apps like Unroll.me (which allows you to unsubscribe from newsletters in bulk) make your life easier. And I get it. I’ve tried them too. But I disconnect them from my email account as soon as I’m done with them.
The thing is that, if you give a third-party app full access to your inbox, this makes you vulnerable to cyber attacks. The app can be compromised and, as a consequence, cyber criminals would gain unhindered access to all your emails and their contents.
If you have to use these apps, disconnect them at soon as you don’t need them.
6. Stop oversharing private information
In today’s connected world, oversharing is the norm. However, you should not compare your online habits to those that most people have, because, to be honest, most people don’t really care about their safety.
By reading this far into the article, you’re definitely the type of person who does care about Internet security. That’s why I trust that you’ll hear my plea to:
- Never share private information on social media networks (where your house is, how big it is, where your relatives live, etc.)
- Never use family names, dates of birth, pet names and the like as passwords
- Never reply to suspicious emails with sensitive information (like your card details, social security number, etc.)
- Never give away your email address to just anyone who asks for it (also, that’s why you should have multiple email addresses)
- Check your email account activity regularly for any suspicious activity
- Not befriend anyone you meet online without questioning their motivations.
Paranoia can be healthy in small doses.
7. Don’t jump connecting to any free public Wi-Fi network
This type of temptation is the strongest during holidays.
You want to just send a quick email with vacation pictures, so you connect to the cafe’s Wi-fi network.
But have you stopped to think about the chance that some low-level cyber crook is manipulating the network to collect usernames and passwords?
Are you really prepared to face an advanced criminal mind, who does this for a living?
No, you’re not.
But since we know you won’t resist the temptation to go into the wild, just don’t do these 2 things: don’t connect to your email address account and don’t run any financial transaction!
I know you can do it!
8. Don’t store default passwords
Often, when you set up a new account using your email address, you’ll receive a default password in plain text in an email. Do yourself a favor and don’t keep the password in your inbox.
Change your default password and delete the email, cutting the chances of a cyber criminal attack which could spread to compromise additional account.
9. Keep your eyes peeled for phishing and scams
Most successful online scams always start with an initial email sent to a potential victim. These scams rely on social engineering techniques that can tricks even the most experienced Internet users.
Train yourself to spot online scams and phishing attempts, which often rely on impersonating trusted entities or people in your life to get you to give up your data.
These are two of the most popular hacking techniques to steal financial information. Usually, there is no other way to stay safe from this malicious attempt aside from preventing the initial infection phase.
As a rule of thumb, follow these simple guidelines:
- don’t click suspicious links in emails
- don’t reply an email if you’re not sure about the sender
- don’t download or click on email attachments that seem unsafe.
10. Keep your software up to date
As I just mentioned, email is usually the first step in the malware infection chain. People simply don’t pay enough attention to the emails they open and what they click on once they’ve opened them. Even malware sent in spam emails still works.
Cyber criminals often use Microsoft Word, Excel, and PowerPoint files to deliver malware to unsuspecting victims.
But if your system is up to date and protected with multiple layers of security, the chances you’ll suffer a cyber attack are significantly lower.
Keeping software up to date is still a core security layer which experts tout as a must-have.
11. Get inside the attacker’s head
Understanding how a cyber criminal thinks can give you strong leverage in building your defenses.
This is an useful exercise to undergo. By the end of this article you’ll never think that your inbox and its contents are worthless. You’ll finally see why attackers are so keen in getting in your inbox and how they can monetize every bit of data you have.
12. Don’t leave your protection to chance. Use available tools
Install a reliable antivirus which also offers real-time protection, back up your data and regularly scan your PC for spyware, keyloggers and other data-stealing malware.
All cyber criminals want is to persuade you to click on a link that will download malware onto your device. In the blink of an eye, the worst-case scenario could unfold with you as a protagonist.
Don’t click the link. Don’t open the spam email. Don’t download the attachment. Satisfying your curiosity is not worth the risk in this case.
So here we are, at the end of a guide that I hope will help you go from “I don’t care about my inbox, there’s nothing valuable in there anyway” to “I’m much more peaceful to know that I’ve boosted my online protection”. Our colleague learned this lesson the hard way, a few years ago.
Do remember that putting the words into action is what makes the difference and keeps you safe.






EASY AND RELIABLE. WORKS WITH ANY ANTIVIRUS.
This post was originally published by Aurelian Neagu in January 2015 and was updated by Andra Zaharia in October 2016.
For more on this story go to: https://heimdalsecurity.com/blog/complete-guide-e-mail-security/